-
摘要:
针对立体图像版权保护问题,提出了一种基于左右视点相关性的立体图像鲁棒水印方法。由于张量分解能够较好保存图像的主要能量,因此,首先利用彩色视点中RGB三通道之间的相关性,对左右视点分别进行张量分解。每一个视点分解出三个特征图,其中每个视点的第一特征图保留了每个视点中较强的三通道关系。其次,结合左右视点之间的相关性,联合左右视点的第一特征图进行张量分解,得到立体图像的主要能量特征图。最后,将主要能量特征图进行奇异值分解,并嵌入水印从而提高鲁棒性。实验结果表明,该方法具有较高的鲁棒性和不可见性,并且实现了水印的盲提取。
 Abstract:
Abstract:To solve the copyright protection of stereo images, a robust stereo image watermarking method based on correlations of left and right views is proposed. Because the tucker decomposition can preserve the main energy of the image well, tucker decomposition is performed on left and right views, respectively, to make full use of the correlations of three channels in the color view. Each view is decomposed into three feature images, where the first feature map retains relationships of three channels in each view. Secondly, considering correlations between the left and right views, the first feature images of the left and right viewpoints are combined to be performed by using tucker decomposition, and the main energy features images of the stereo image are obtained. Finally, the main energy feature image is decomposed by singular value decomposition, and watermark is embedded for the purpose of improving the robustness. Experimental results show that the proposed method has high robustness and invisibility, and realizes blind extraction of watermark.
-
Key words:
- stereo image /
- robust watermarking /
- tucker decomposition /
- correlation /
- blind extraction
-

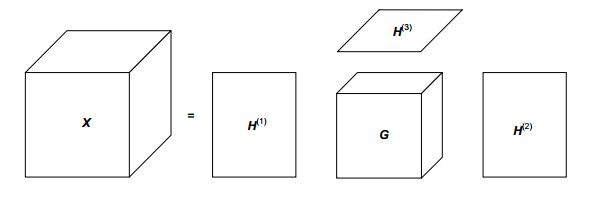
Overview: With the development of network and multimedia technology, two dimensional (2D) image or video has become ubiquitous in all aspects of people's life, and real-time 2D video visual communication has matured. However, the 2D video cannot meet the visual requirements of people. The 3D realism has gradually become a fashion pursuit, since 3D images or videos provide the depth information of the scene and enhance the sense of reality. The demand for the development and applications of the 3D video system in the market is becoming much more urgent. It has a wide range of applications prospects in many fields such as stereoscopic digital television, distance education, 3D video conference system, virtual reality system, telemedicine, etc. With the popularity of 3D videos or images, 3D multimedia content may be transmitted through the Internet and other non-secure channels, and they may be copied, tampered or illegally used. It is essential to prevent illegal dissemination of 3D multimedia information, and watermarking as embedding the secret data into the 3D images is the main technology of protecting copyright. So far, the robust watermarking method for the monocular image is almost mature, but only a few stereo image robust watermarking methods are reported. As shown in Fig, to solve the copyright protection of stereo images, a robust stereo image watermarking method based on correlations of left and right views is proposed. Because Tucker decomposition can preserve the main energy of the image well, it is performed on left and right views to make full use of the correlations of three channels in the color view. Each view is decomposed into three feature images, where the first feature map retains relationships of three channels in each view. Secondly, considering correlations between the left and right views, the first feature images of the left and right views are combined to be performed by using Tucker decomposition, and the main energy features images of the stereo image are obtained. Finally, the main energy feature image is decomposed by singular value decomposition, and watermark is embedded for the purpose of improving the robustness. The experimental results show that when different kinds of stereo images are attacked by Convolution Filter, JPEG compression, Median Filter, Scaling and Cropping, watermark can be extracted blindly, and recognized with high NC. Compared with the monocular image watermarking methods, the proposed algorithm is more robust.
-
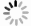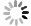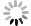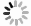
-
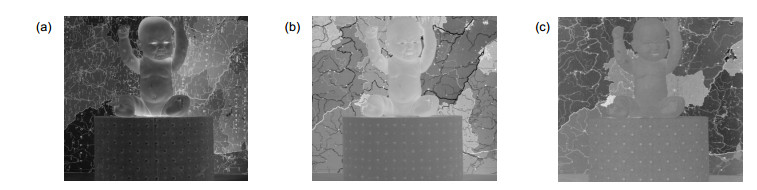
图 7 击后提取的水印图像。(a) Conv1(NC=0.9249); (b) Conv2(NC=0.9655);(c) JPEG90(NC=0.9884); (d) Scaling0.9(NC=0.9271); (e) Scaling2(NC=0.9781); (f) Cropping0.95(NC=0.9911)
Figure 7. Extracted watermark image after attack. (a) Conv1(NC=0.9249); (b) Conv2(NC=0.9655); (c) JPEG90(NC=0.9884); (d) Scaling0.9(NC=0.9271); (e) Scaling2(NC=0.9781); (f) Cropping0.95(NC=0.9911)
表 1 各立体图像的PSNR和SSIM
Table 1. PSNR and SSIM of all stereoscopic image
Image Proposed Method 1 Left view Right view PSNR SSIM PSNR SSIM PSNR SSIM Baby1 42.12 1.0000 42.28 1.0000 42.20 1.0000 Bowling1 43.81 1.0000 44.04 1.0000 43.99 1.0000 Art 43.54 1.0000 43.66 0.9999 44.00 1.0000 Dolls 41.43 1.0000 41.48 0.9999 41.49 1.0000 表 2 攻击参数
Table 2. Attack parameters
Attack Parameter value Convolution filter Window size=3×3 Conv1:a=1/9, b=2/9, c=1/9, d=2/9, e=4/9, f=2/9, g=1/9, h=2/9, i=1/9 Conv2:a=0, b=-1/9, c=0, d=-1/9, e=5/9, f=-1/9, g=0, h=-1/9, i=0 JPEG compression Quality factor: 50, 90 Median filter Window size: 3×3, 5×5 Scaling Ratio (on each side): 0.9, 1.1, 1.5, 2 Cropping Retain ratio (on each side): 0.71, 0.78, 0.84, 0.9, 0.95 表 3 所有视点攻击后提取水印的NC
Table 3. NC of all views by different attacks
Attack Baby Bowling Art Dolls Proposed Method 1 Proposed Method 1 Proposed Method 1 Proposed Method 1 Conv1 0.9416 0.9320 0.9744 0.9695 0.9464 0.9451 0.9270 0.9214 Conv2 0.9748 0.9711 0.9972 0.9955 0.9888 0.9803 0.9861 0.9809 JPEG90 0.9693 0.9542 0.9548 0.9531 0.9612 0.9150 0.9839 0.9781 JPEG50 0.7124 0.7268 0.7601 0.7737 0.7132 0.7224 0.7381 0.7748 Median3×3 0.9776 0.9677 0.9929 0.9921 0.9764 0.9150 0.9586 0.9474 Median5×5 0.9721 0.9642 0.9924 0.9929 0.9769 0.9725 0.9601 0.9515 Scaling0.9 0.9461 0.9406 0.9634 0.9571 0.9461 0.9405 0.9341 0.9340 Scaling1.1 0.9737 0.9723 0.9849 0.9810 0.9721 0.9711 0.9704 0.9646 Scaling1.5 0.9766 0.9728 0.9862 0.9821 0.9745 0.9736 0.9723 0.9634 Scaling2 0.9762 0.9727 0.9861 0.9822 0.9744 0.9729 0.9723 0.9629 Cropping0.71 0.9261 0.9014 0.9253 0.8999 0.9215 0.8958 0.9230 0.8961 Cropping0.78 0.9392 0.9227 0.9382 0.9210 0.9341 0.9187 0.9370 0.9187 Cropping0.84 0.9550 0.9353 0.9548 0.9338 0.9502 0.9303 0.9526 0.9303 Cropping0.9 0.9695 0.9594 0.9698 0.9575 0.9664 0.9566 0.9685 0.9568 Cropping0.95 0.9842 0.9786 0.9835 0.9769 0.9800 0.9765 0.9831 0.9764 Average 0.9455 0.9381 0.9576 0.9512 0.9455 0.9324 0.9445 0.9372 表 4 算法结果比较
Table 4. Comparison of algorithm result
Attack Ref. [19] Proposed JPEG90 0.9766 0.9673 Gaussian low pass3×3 0.9899 0.9929 Median3×3 0.9132 0.9764 Average3×3 0.9327 0.9666 Cropping1/8 0.8766 0.9904 Cropping1/4 0.7462 0.9955 Cropping1/2 0.4909 0.9891 -
[1] Schierl T, Narasimhan S. Transport and storage systems for 3-D video using MPEG-2 systems, RTP, and ISO file format[J]. Proceedings of the IEEE, 2011, 99(4): 671-683. doi: 10.1109/JPROC.2010.2091370
[2] Zhang L, Vazquez C, Knorr S. 3D-TV content creation: automatic 2D-to-3D video conversion[J]. IEEE Transactions on Broadcasting, 2011, 57(2): 372-383. doi: 10.1109/TBC.2011.2122930
[3] Jiang L L, He J Q, Zhang N, et al. An overview of 3D video representation and coding[J]. 3D Research, 2010, 1(1): 43-47. doi: 10.1007/3DRes.01(2010)6
[4] Smolic A, Mueller K, Stefanoski N, et al. Coding algorithms for 3DTV—a survey[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2007, 17(11): 1606-1621. doi: 10.1109/TCSVT.2007.909972
[5] 张宪海, 杨永田.基于脆弱水印的图像认证算法研究[J].电子学报, 2007, 35(1): 34-39. doi: 10.3321/j.issn:0372-2112.2007.01.007
Zhang X H, Yang Y T. Image authentication scheme research based on fragile watermarking[J]. Acta Electronica Sinica, 2007, 35(1): 34-39. doi: 10.3321/j.issn:0372-2112.2007.01.007
[6] 王国栋, 刘粉林, 刘媛, 等.一种能区分水印或内容篡改的脆弱水印算法[J].电子学报, 2008, 36(7): 1349-1354. doi: 10.3321/j.issn:0372-2112.2008.07.019
Wang G D, Liu F L, Liu Y, et al. An image authentication scheme with discrimination of tampers on watermark or image[J]. Acta Electronica Sinica, 2008, 36(7): 1349-1354. doi: 10.3321/j.issn:0372-2112.2008.07.019
[7] 刘东彦, 刘文波, 张弓.图像内容可恢复的半脆弱水印技术研究[J].中国图象图形学报, 2010, 15(1): 20-25. 10.11834/jig.20100104
Liu D Y, Liu W B, Zhang G. Research of recoverable semi-fragile watermarking for image content[J]. Journal of Image and Graphic, 2010, 15(1): 20-25. 10.11834/jig.20100104
[8] 白韬韬, 刘真, 卢鹏.基于QR码的Contourlet域数字水印算法[J].光电子•激光, 2014, 25(4): 769-776. http://www.cqvip.com/QK/92586A/201404/49429841.html
Bai T T, Liu Z, Lu P. Digital watermarking scheme in Contourlet domain based on QR code[J]. Journal of Optoelectronics • Laser, 2014, 25(4): 769-776. http://www.cqvip.com/QK/92586A/201404/49429841.html
[9] 王晓红, 孙业强.基于QR码和Schur分解的感兴趣区域水印算法[J].光电子•激光, 2017, 28(4): 419-426. http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=QKC20172017051200047662
Wang X H, Sun Y Q. Region of interest based watermarking algorithm based on QR code and Schur decomposition[J]. Journal of Optoelectronics • Laser, 2017, 28(4): 419-426. http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=QKC20172017051200047662
[10] 任克强, 张丹丹, 吴帆.融合DCT和汉明码的自适应鲁棒图像水印[J].光电工程, 2016, 43(11): 54-61. doi: 10.3969/j.issn.1003-501X.2016.11.009
Ren K Q, Zhang D D, Wu F. Adaptive robust image watermarking based on DCT and Hamming code[J]. Opto-Electronic Engineering, 2016, 43(11): 54-61. doi: 10.3969/j.issn.1003-501X.2016.11.009
[11] Chen H Y, Zhu Y S. A robust watermarking algorithm based on QR factorization and DCT using quantization index modulation technique[J]. Journal of Zhejiang University-Science C, 2012, 13(8): 573-584. doi: 10.1631/jzus.C1100338
[12] 叶天语.离散小波变换域鲁棒量化灰度水印算法[J].光电工程, 2012, 39(7): 120-125. doi: 10.3969/j.issn.1003-501X.2012.07.019
Ye T Y. A robust quantization-based Gray watermarking algorithm in discreet wavelet transform domain[J]. Opto-Electronic Engineering, 2012, 39(7): 120-125. doi: 10.3969/j.issn.1003-501X.2012.07.019
[13] Kang X B, Zhao F, Lin G F, et al. A novel hybrid of DCT and SVD in DWT domain for robust and invisible blind image watermarking with optimal embedding strength[J]. Multimedia Tools and Applications, 2018, 77(11): 13197-13224. doi: 10.1007/s11042-017-4941-1
[14] Cedillo-Hernández M, García-Ugalde F, Nakano-Miyatake M, et al. Robust hybrid color image watermarking method based on DFT domain and 2D histogram modification[J]. Signal Image and Video Processing, 2014, 8(1): 49-63. doi: 10.1007/s11760-013-0459-9
[15] Sun L, Xu J C, Liu S W, et al. A robust image watermarking scheme using Arnold transform and BP neural network[J]. Neural Computing and Applications, 2018, 30(8): 2425-2440. doi: 10.1007/s00521-016-2788-4
[16] Liu N S, Li H J, Dai H Y, et al. Robust blind image watermarking based on chaotic mixtures[J]. Nonlinear Dynamics, 2015, 80(3): 1329-1355. doi: 10.1007/s11071-015-1946-z
[17] Luo T, Jiang G Y, Wang X D, et al. Stereo image watermarking scheme for authentication with self-recovery capability using inter-view reference sharing[J]. Multimedia Tools and Applications, 2014, 73(3): 1077-1102. doi: 10.1007/s11042-013-1435-7
[18] Campsi P. Object-oriented stereo-image digital watermarking[J]. Journal of Electronic Imaging, 2008, 17(4): 043024. doi: 10.1117/1.3009554
[19] Wu A H, Yu M, Peng Z J, et al. Relationship modulation based blind stereoscopic image watermarking algorithm for 3D media[C]// International Conference on Internet Technology and Applications. Wuhan, 2011: 1-4.
[20] Ou Z H, Chen L H. A robust watermarking method for stereo-pair images based on unmatched block bitmap[J]. Multimedia Tools and Applications, 2016, 75(6): 3259-3280. doi: 10.1007/s11042-014-2433-0
[21] Vo P H, Nguyen T S, Huynh V T, et al. A robust hybrid watermarking scheme based on DCT and SVD for copyright protection of stereo images[C]// Proceedings of the 4th NAFOSTED Conference on Information and Computer Science. Hanoi, 2017: 331-335.
-

 E-mail Alert
E-mail Alert RSS
RSS
 下载:
下载: